How Edge Networks Connect to ISPs
How do Edge Networks Connect to ISPs?
Edge networks physically connect end systems to their respective routers on a path to other end systems via Access Networks[^1]. In short, an access network is a type of communications network which allows the connection of edge networks (AKA hosts or clients) to their respective Internet Service Providers. It is for this reason that access networks are considered the "last leg" of telecommunications networks[^2]. The connective purpose of access networks is in clear contrast to a Core Network's, which connects local providers with each other.

In this figure, you can see access networks represented as thick, shaded lines that connect edge systems to their routers. You can also see the various types of access networks, which we will explore below.
Enterprise Networks
Connects end systems on the LAN to applications in the data center and the cloud as well as giving data access and analyses through networks and protocols that exist physically and virtually. It provides fast and reliable connectivity in an increasingly distributed modern network and provides more security.
Perimeter and internal firewalls as well as the configurations of said firewalls are an essential part of enterprise networking as it can prevent attacks on apps and data from the outside such as viruses or malware. Advanced internal firewalls offer the ability to deliver seamless connectivity across hybrid and multi-cloud segmented networks and to secure those networks with inspection of all traffic. Security administrators should always seek more advanced methods to scan data packets to improve security as phishing attacks and ransomware could lead to very detrimental consequences to an organization.
Enterprise networking should always have networking solutions that supports the organization’s workflow, production processes, consumer demand, logistics, etc. A good network can achieve increased efficiency through collaboration as employees can work together on shared resources, controlled and secured access to company's resources by the existence of firewalls, higher productivity through streamlined test/dev with collaboration tools and version control, and lower costs due to server and network virtualization[^3].
Home Networks
Connects end systems to the internet or to each other by wires (LAN) or wirelessly (such as modems), most prominent in homes. Suitable for day-to-day connections between systems[^4]. Here are some examples of how homes connect to the internet.
- Digital Subscriber Line (DSL)[^1]
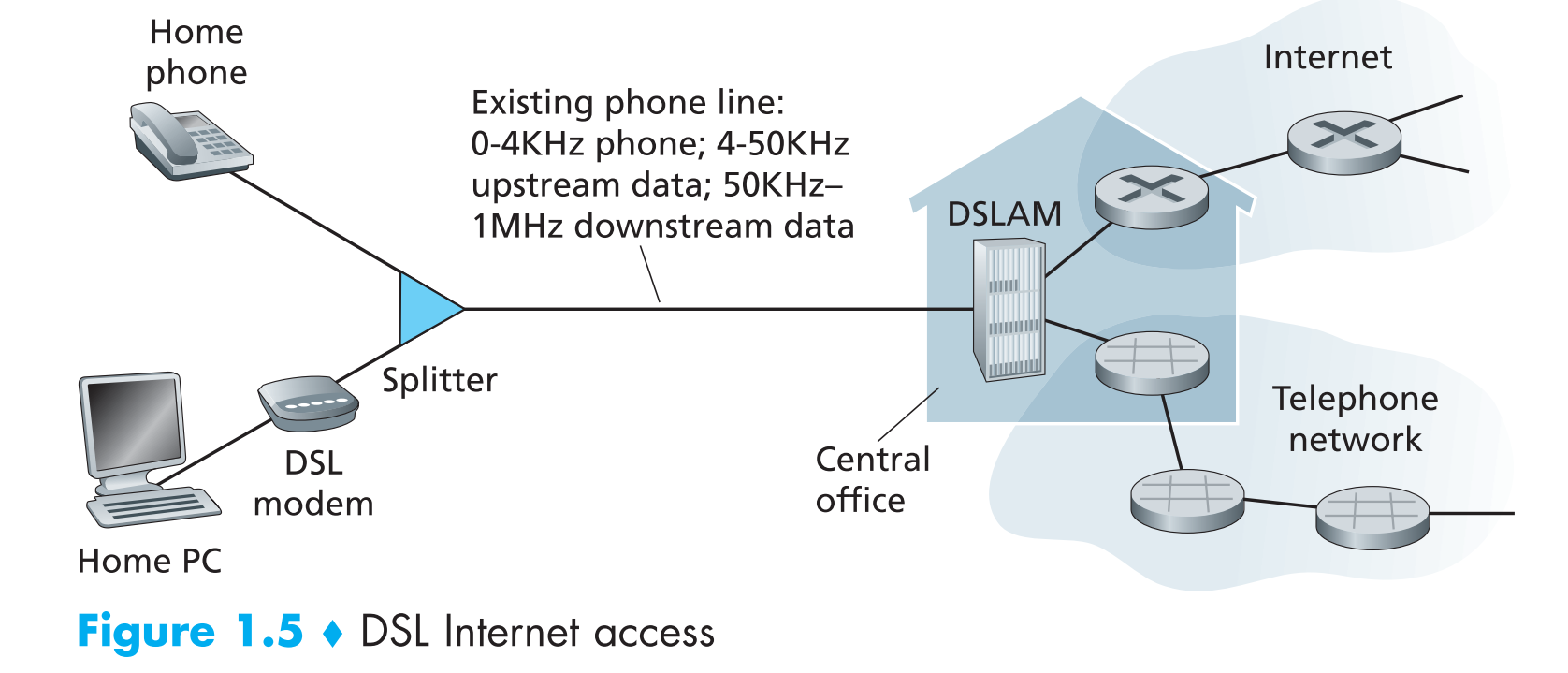
DSL Internet Access used existing telephone line to telco's central office Digital Subscriber Line Access (DSLAM). The telephone line carries data and telephone signal simultaneously at different frequencies. The Splitter separates the data and the telephone signal, the data goes to the internet and the telephone signal goes to telephone net.
- Cable-based Access[^1]
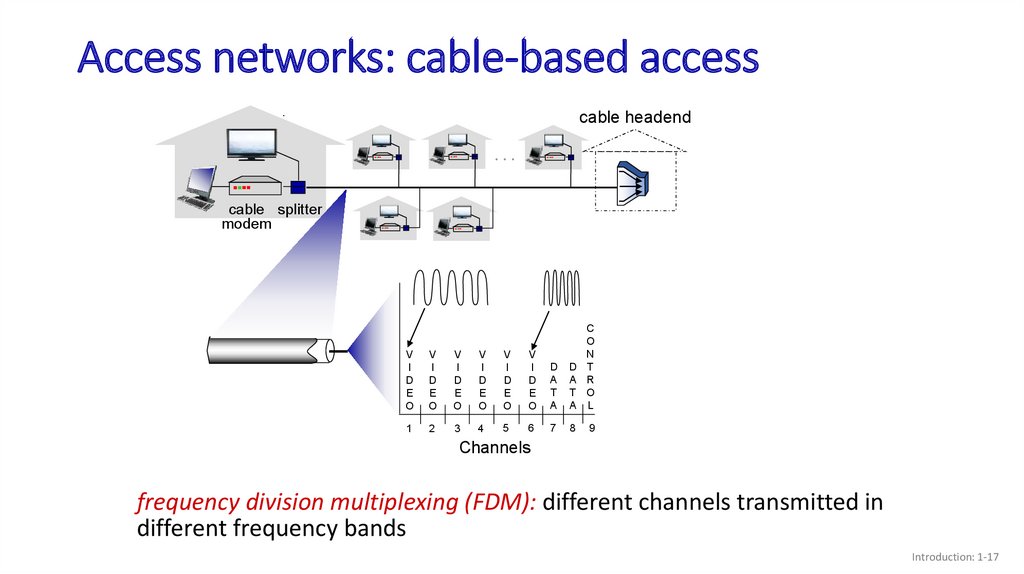
Cable Internet access makes use of the cable television company’s existing cable television infrastructure. Cable internet access requires cable modems. At the cable head end, the Cable Modem Termination System (CMTS) serves similar function with DSLAM in DSL Internet Access. Cable internet access is a shared-broadcast medium, meaning network is a bus shared by many home. Consequently, users may not get full speed if there are many users simultaneously using the connection.
Content Provider Networks
Also known as Content Delivery Network (CDN), connects end users to highly-distributed servers containing cached versions of internet contents (such as websites) in multiple geographical locations around the world, also known as Points of Presence (PoPs). Through this, users of end systems can view said contents with high-quality reduced delays or traffics[^5].
Wire-Area Wireless Networks (Mobile Networks / Wireless WAN)
Connects to end systems wirelessly over a wide geographic area with the use of multiple cell sites (usually in a form of towers) or base transceiver stations, each one of them covers land areas called cells. The higher the population within the area, the more cell sites are needed[^6].
Wide-area wireless networks provide the benefit of providing network access within tens of kilometers from the nearest cellular station; as opposed to being restricted within being a few tens of meters in the case of WiFi connectivity. This is an area of edge network connectivity which is undergoing a major advancement in recent days, with the advent of higher speed 5G connectivity; expanding upon existing GSM, 2G, 3G, and 4G networks[^7].
In the past, mobile networks have faced criticism regarding its security. This stems from the fact that wireless communication systems do not provide a physically secure connection path. In response to this, modern mobile networks utilize encryption and authentication methods to secure ongoing communications. While early forms of these encryption techniques were flawed in one way or another[^8], modern day mobile networks are generally considered much more secure than their early predecessors.
References
[^1]: Kurose, J.F. and Ross, K.(2021) Computer Networking: A Top-Down Approach. (8th ed., pp. 12-18). Pearson.
[^2]: Ramaswami et al. (2010) Optical Networks (3rd ed.), abridged in ScienceDirect
[^3]: What is Enterprise Networking? | VMware Glossary. https://www.vmware.com/topics/glossary/content/enterprise-networking
[^4]: What is Home Networking? - Xfinity Support. https://www.xfinity.com/support/articles/what-is-home-networking
[^5]: What does CDN stand for and how does it work? | Akamai. https://www.akamai.com/us/en/cdn/what-is-a-cdn.jsp
[^6]: Cellular network - Wikipedia. https://en.wikipedia.org/wiki/Cellular_network
[^7]: Mobile Broadband - Wikipedia. https://en.wikipedia.org/wiki/Mobile_broadband
[^8]: Digital Cell Phone Crypto Cracked - Wired. https://www.wired.com/1997/03/digital-cell-phone-crypto-cracked/